IT Company Blog
latest tech news with IT Company
Engage & Learn through Tech, IT Support Services, Website Security, Business and many more.











Other Articles
Decoding Affordable Hosting Program for Website Management
In today’s digital world, having a dependable Hosting program is critical to the success of your online presence. WordPress-optimized hosting…
7 Winning Strategies to Save Time & Resources with API Solution
Businesses are always looking for new ways to simplify operations, save time, and optimise resources. APIs are the foundation of…
How to Automate Business Processes with Microsoft Office 365
Microsoft Office 365 includes a number of technologies for automating corporate operations, such as Power Automate, Microsoft Flow, and SharePoint.…
Top 10 Winning Web Maintenance Practices for SEO
Welcome to our blog to find top 10 best Web Maintenance methods for achieving your SEO objectives! In today’s competitive online…
How to Implement Email Security Check Policies in an Organization
In the modern age, where cyber risks occur and privacy breaches are an ongoing problem, protecting your organization’s email communication…
How to Design a Scalable API Solution for Growing Businesses
Starting the process of expanding your business may be both exciting and terrifying. As your client base grows and your…
How to Identify and Repair Website Issues after Updating WordPress in 2024?
If your WordPress website fails after activating a certain plugin or theme, you can reactivate it with PHPMyAdmin. If removing…
How to Enable WordPress Two-Factor Authentication for Online Website Security
What exactly is two-factor authentication in WordPress? Two-factor authentication (2FA) is a security feature for WordPress that helps to Online…
How to Find and Fix Broken Authentication Vulnerability
Broken authentication is a vulnerability in security that happens when a program fails to properly authorize its users. This can…
How to Implement Real-time Data Sync with API Integration
Let’s dive a little deeper. Realtime does not always imply that anything is updated instantaneously (there is no one meaning…
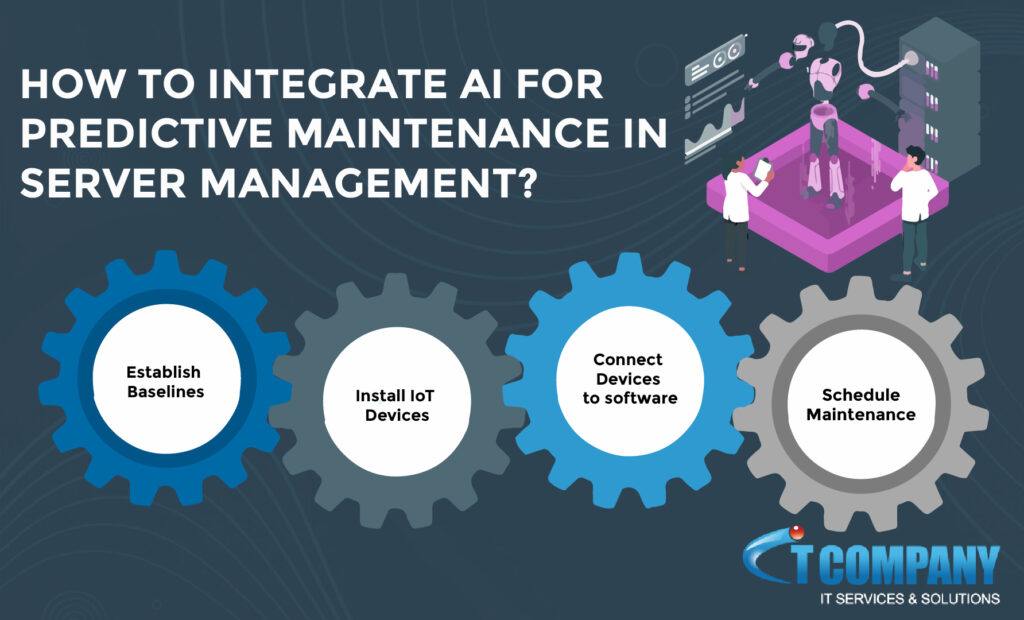
How to Integrate AI for Predictive Maintenance in Server Management
Server management is a critical aspect of any organization’s IT infrastructure. In today’s fast-paced digital world, the ability to predict…
WordPress Sites Infected with Balada Injector Malware Campaign
Since 2017, it’s been reported that over a million WordPress websites have been infected by malware known as Balada Injector.…