
Table of Contents
ToggleWelcome to our detailed article on repairing vulnerabilities detected by our Website security tester offers cutting-edge security testing that detects vulnerabilities in your website’s defenses, allowing you to take proactive actions against possible attackers. In this blog, we’ll discuss the necessity of patching vulnerabilities and give step-by-step instructions for dealing with them.
Identifying vulnerabilities
The first step in fixing vulnerabilities is determining where they exist and their severity. Scan your network, devices, apps, and databases for known vulnerabilities, such as CVEs. Some tools are automatically operated, while others require user input. You should also keep an eye on your logs, alerts, and reports for any indicators of suspicious or unusual activity that might point to a breach.

Regular assessments using third-party security technologies are critical for remaining informed and monitoring the vulnerability identification process. Before deploying any new fixes, you must first understand your system’s possible weaknesses. This proactive strategy provides a thorough assessment of your security landscape.
Give preference to patches
Once you’ve compiled a list of vulnerabilities, prioritise them based on their severity, urgency, and feasibility. You can use a scoring system like CVSS (Common Vulnerability Scoring System) to rate vulnerabilities based on their severity and remediation level using Website security tester. You should also examine the importance of the impacted assets, the availability of patches, and the potential adverse effects of applying them. Patch the most significant and urgent vulnerabilities first, then move on to the less crucial ones.
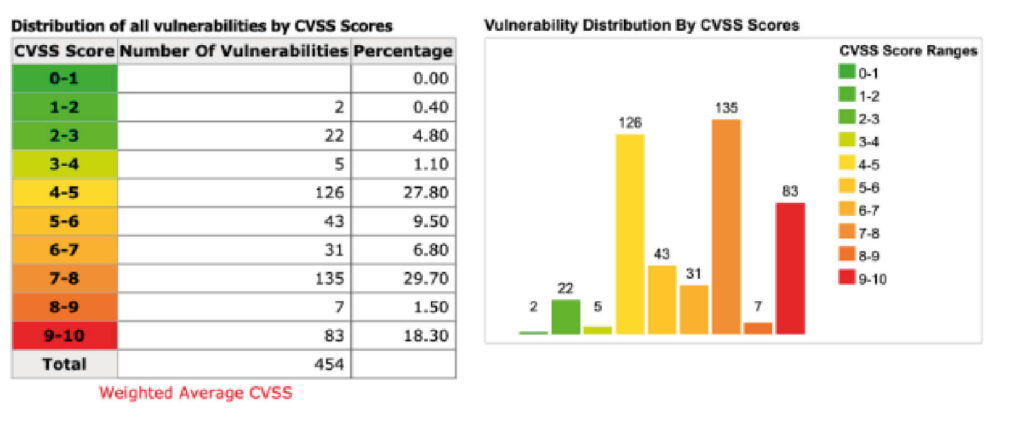
Prioritising vulnerabilities is vital because it allows organisations to focus their resources on addressing significant risks. Prioritising vulnerabilities is critical since it helps to reduce the risk of a data breach or cyber attack on an organization’s most valuable assets.
Testing Patches
Before applying updates to your production system, test them in a different or isolated environment, such as a sandbox or virtual machine. This will allow you to ensure that the fixes operate as intended, that they do not create compatibility difficulties, performance degradation, or feature loss, and that they do not add new vulnerabilities or errors. You should also document the testing procedure and outcomes, as well as prepare a backup plan in case something goes wrong.

Use patches after Test
When it is time to apply patches to your production environment, you should follow a patch management policy and process that specifies the roles, responsibilities, timescales, and actions required. You should also inform your stakeholders, which include users, managers, and vendors, on the patching timeline, scope, and effect. Patches should be applied in batches or phases, beginning with the least crucial or dangerous ones and constantly monitored for outcomes. You should also record the patching procedure and results, as well as having a fail-safe strategy in place.
First and foremost, actions must be made to provide resistance to a certain class of vulnerabilities. Most techniques are reactive, while bad actors are proactive. Most vulnerabilities are discovered after the damage has already been done. The use of containers and sandboxes can assist restrict the breadth of harm until the vulnerability is found, prioritised, and patched.
Verify patches
After applying fixes, you should ensure that they were properly installed, that the vulnerabilities were fixed, and that there were no negative consequences. You may scan your system again with the same tools and methodologies you used to find vulnerabilities and compare the results. Also review your logs, alerts, and reports for any anomalies or issues that may suggest a problem. You should also collect input from users, managers, and suppliers on the patching process and performance.
Keep patches updated

Patching vulnerabilities is an ongoing process that involves frequent maintenance and upgrades, rather than a one-time occurrence. Keep track of the fixes you’ve applied, the patches that are available, and the patches that are still pending. You should also assess your patch management policy and practice on a regular basis and make necessary changes. You should also be aware of the most recent cybersecurity trends and dangers, as well as the best practices and suggestions of experts and authorities.
Conclusion
Finally, Protecting the security of your website is critical with modern technology. Using our Website security tester service provides valuable insight into vulnerabilities that compromise your website’s security.
A web application and website can be scanned in five steps: setting up the scanner, scanning the application for vulnerabilities, having a security analyst prioritise vulnerabilities based on business risk, delivering scan results and assessments, and remediating and testing vulnerabilities.
What is a patch? Patches are software and operating-system (OS) upgrades that fix security flaws in a programme or product. Software makers may opt to offer updates to address performance issues as well as improve security features.
It is an automated method that identifies prospective or known vulnerabilities that threat actors might exploit. Patching is the use of a vendor-supplied or internally produced security patch or fix to address a known vulnerability.





